OPNsense AT&T Gateway Bypass
All I wanted was a graph of real-time broadband utilization of my household. A fully Unifi‘ed network sure looks pretty, but USG just couldn’t do it. Times have changed. Many home networks are wired up for 1.0 Gbps, and today’s open source firewalls have the features I need. Like real-time traffic graphs. My trusty USG served me well for years, but off to the ebay it goes.
In its place, I put together some OPNsense hardware and configured it to bypass AT&T Fiber CPE (BW210-700). Here’s how I did it.
First the easy part: purchase and assemble the hardware.
QOTOM Q555G6 Intel i5 mini PC
8GB DRAM
128GB SSD
USB Thumb drive
I bought a barren mini PC separately from the DRAM and SSD to get the components I thought best. You can also buy a fully-assembled configuration (like this one) or, if you have an unused PC (with sufficiently beefy CPU and at least 3 NIC cards) lying around, you can use that. Just make sure the ethernet hardware is compatible with OPNsense.
Bootable USB drive
Since the raw hardware above comes with no software installed, follow the well written instructions from OPNsense to prepare an USB boot drive - for qotom q555G6, select architecture amd64, and image type of vga.
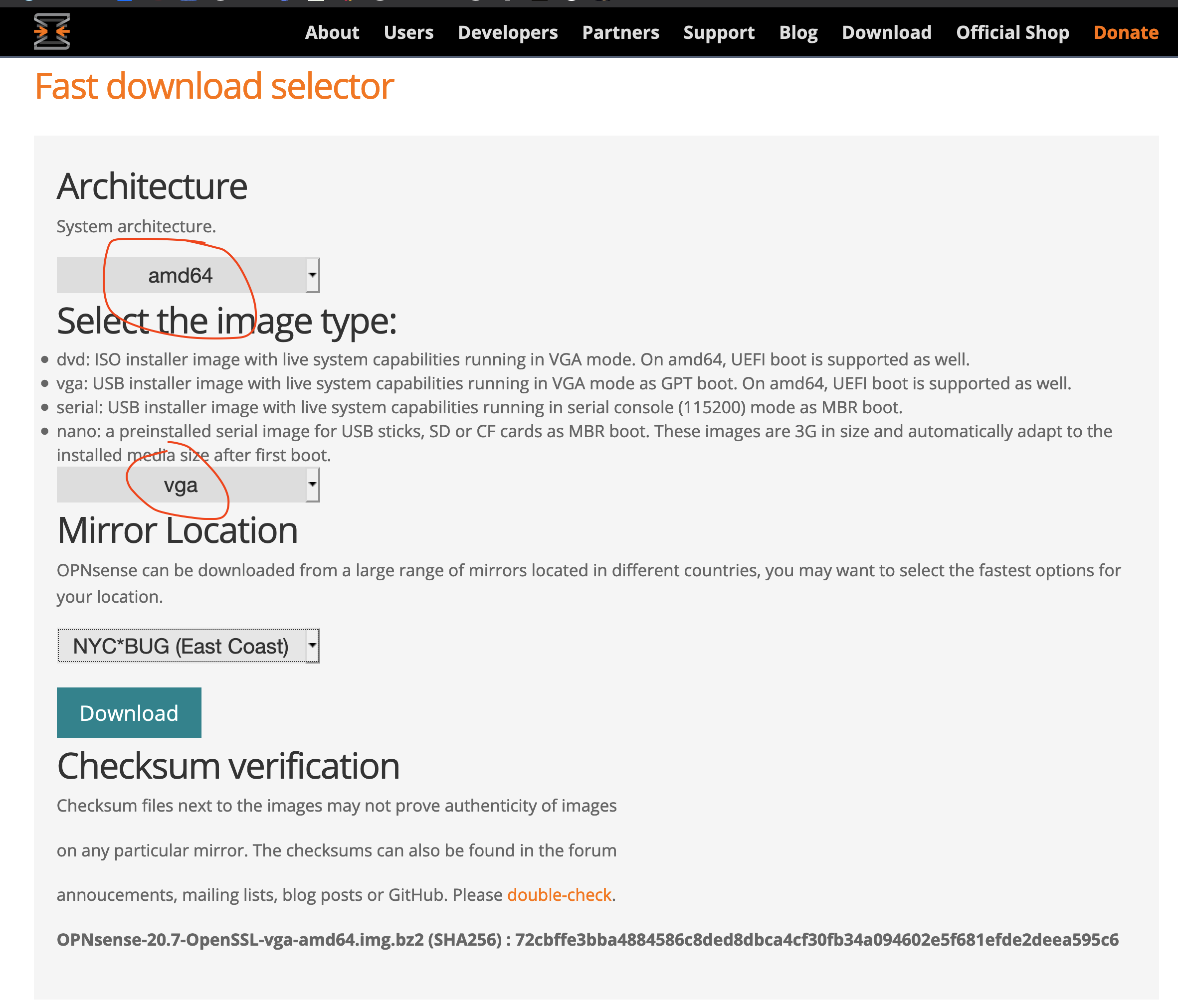
OPNsense configuration
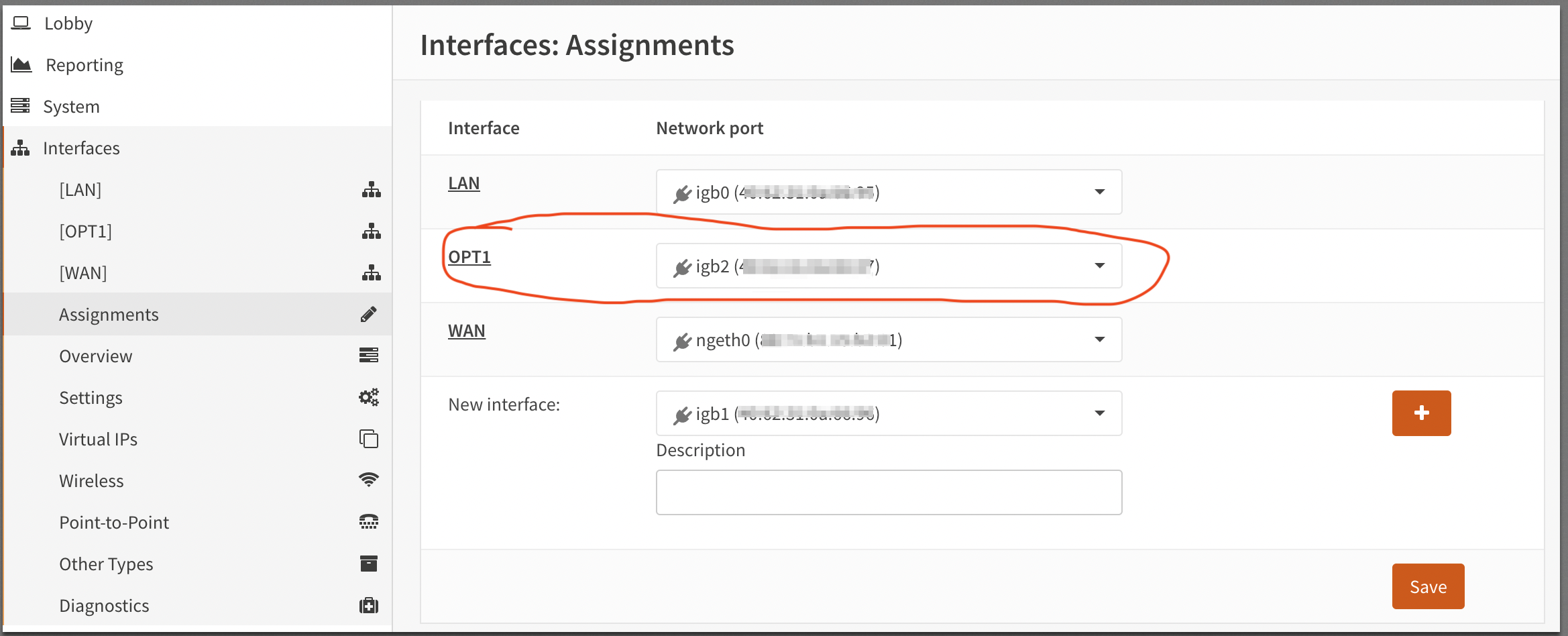
Initial factory installation enables two network interfaces LAN and WAN. We add one more and name it OPT1:
Next, simply follow the instructions from project pfatt README. Because it was written with pfSense in mind, be sure to note the instructions specific to OPNsense:
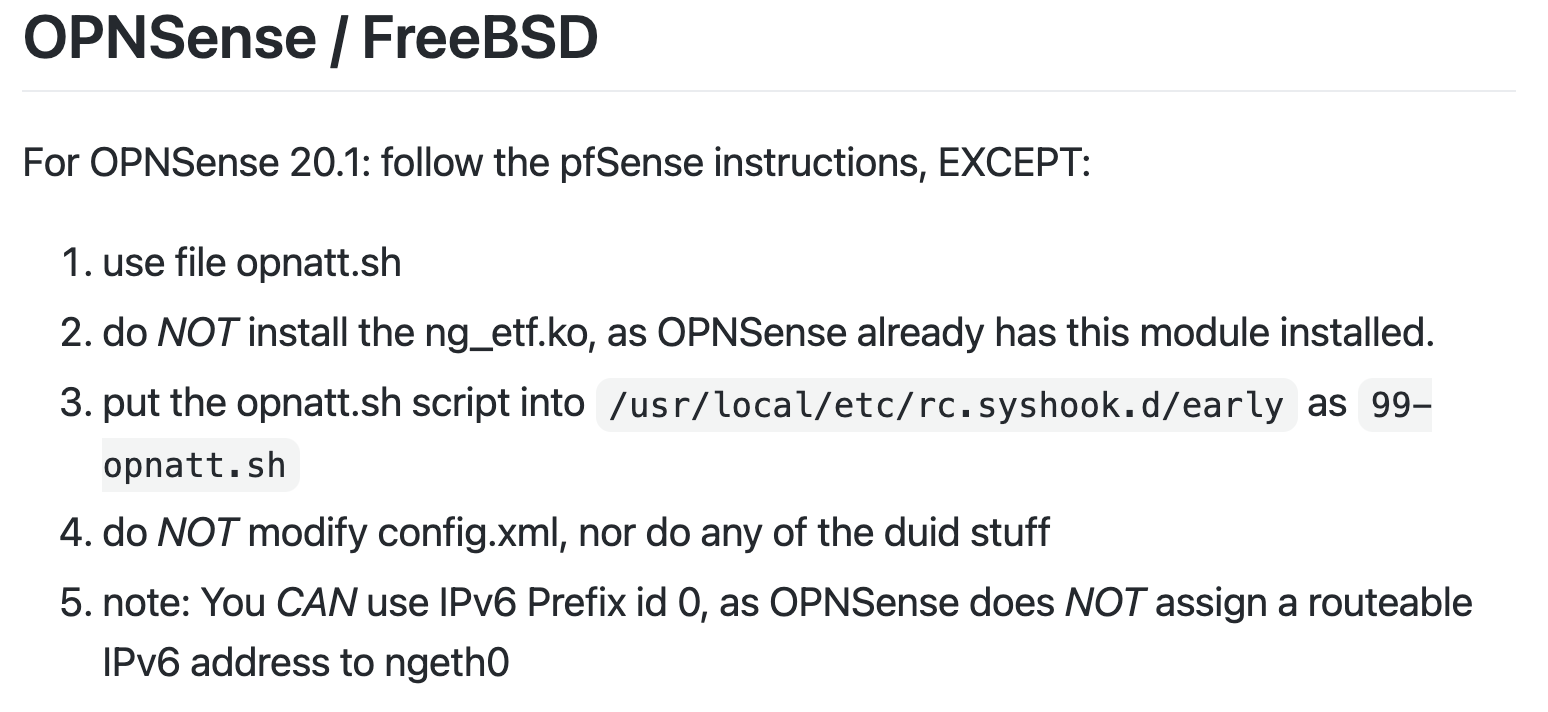
opnatt.sh
OPNsense configuration steps are nearly identical to pfSense. For the qotom hardware, opnatt.sh modification are below.
ONT_IF='igb1' # NIC -> ONT / Outside
RG_IF='igb2' # NIC -> Residential Gateway's ONT port
RG_ETHER_ADDR='99:55:b2:23:a4:45' # MAC address of Residential Gateway
LOG=/var/log/opnatt.log
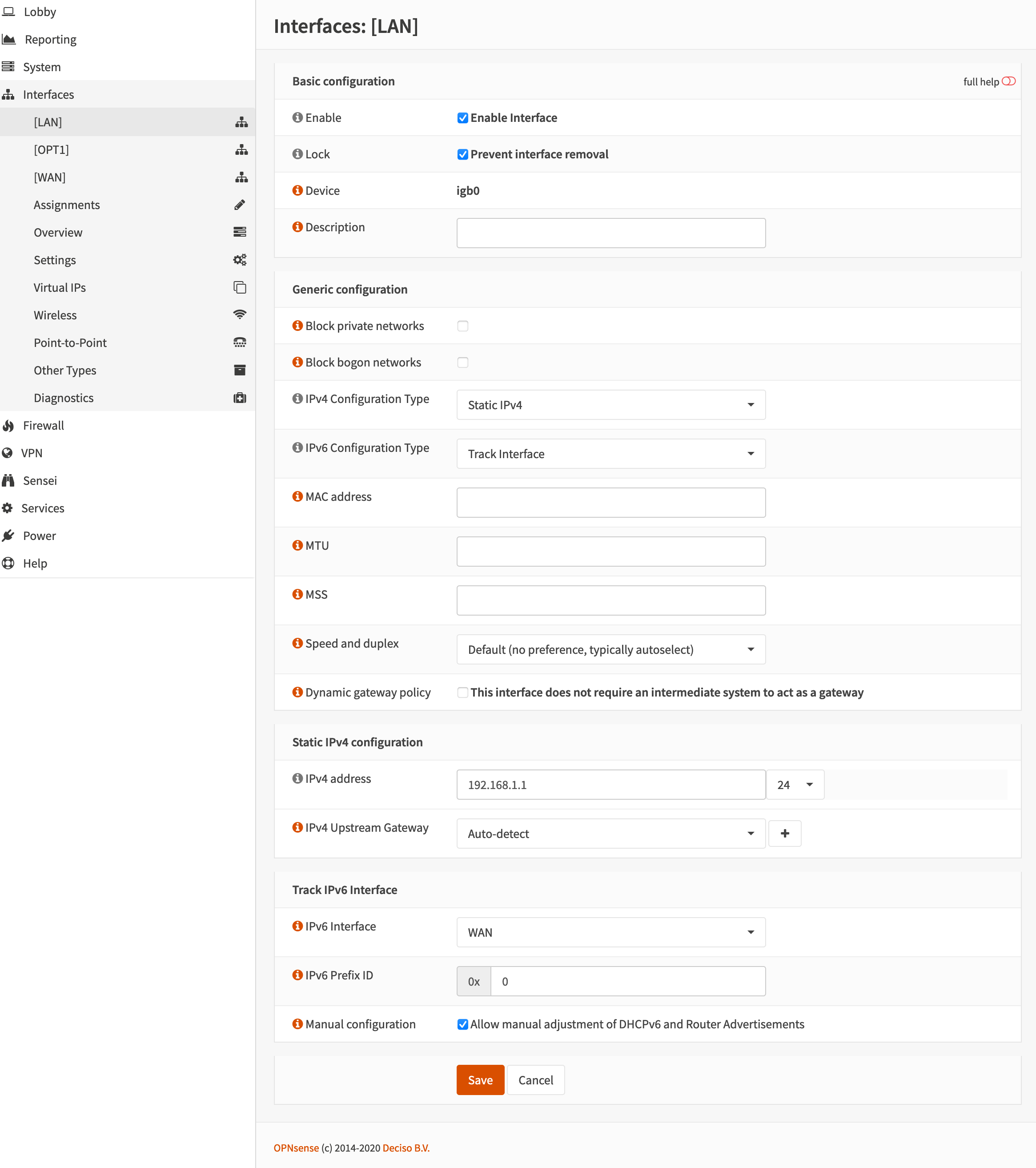
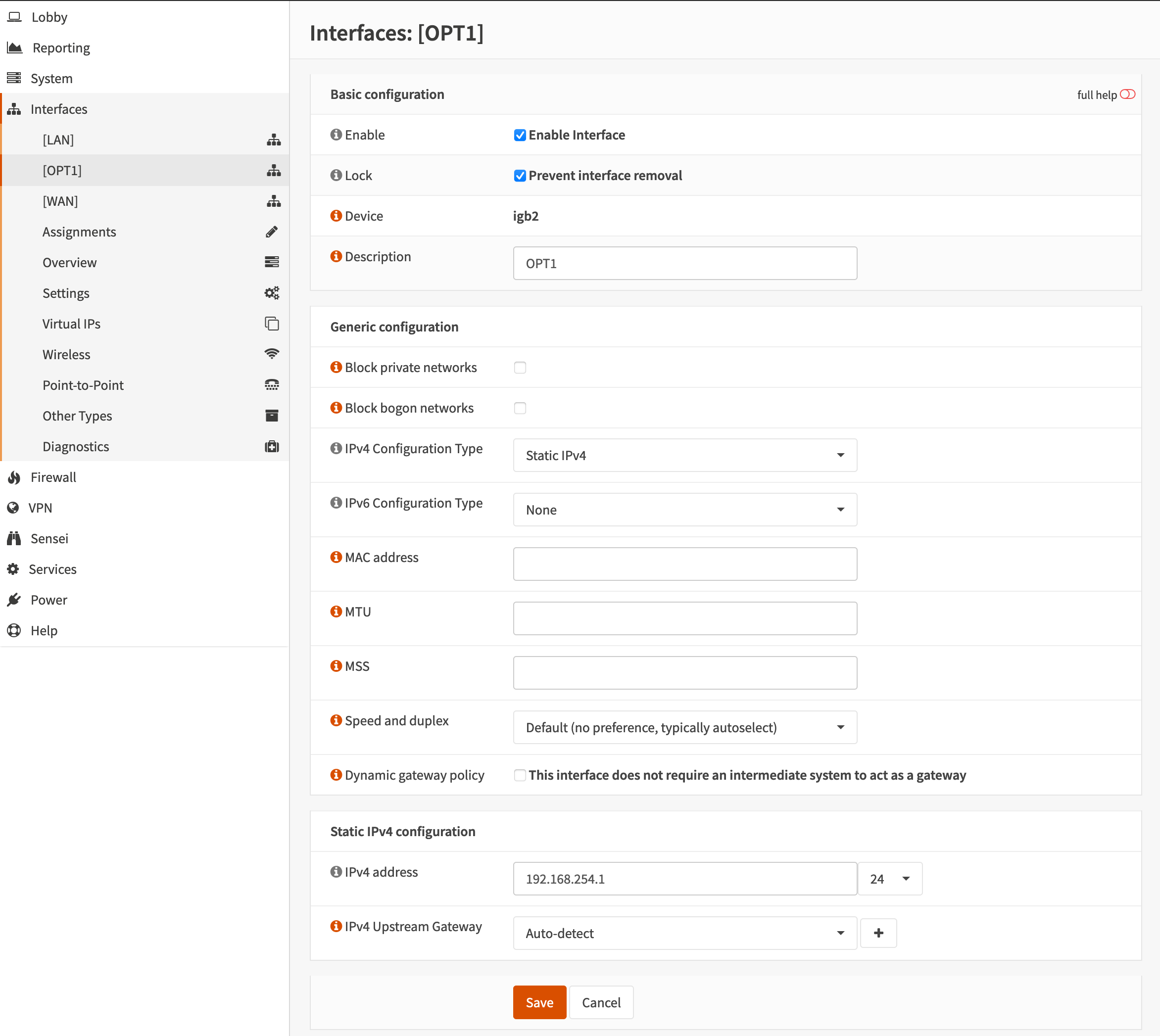
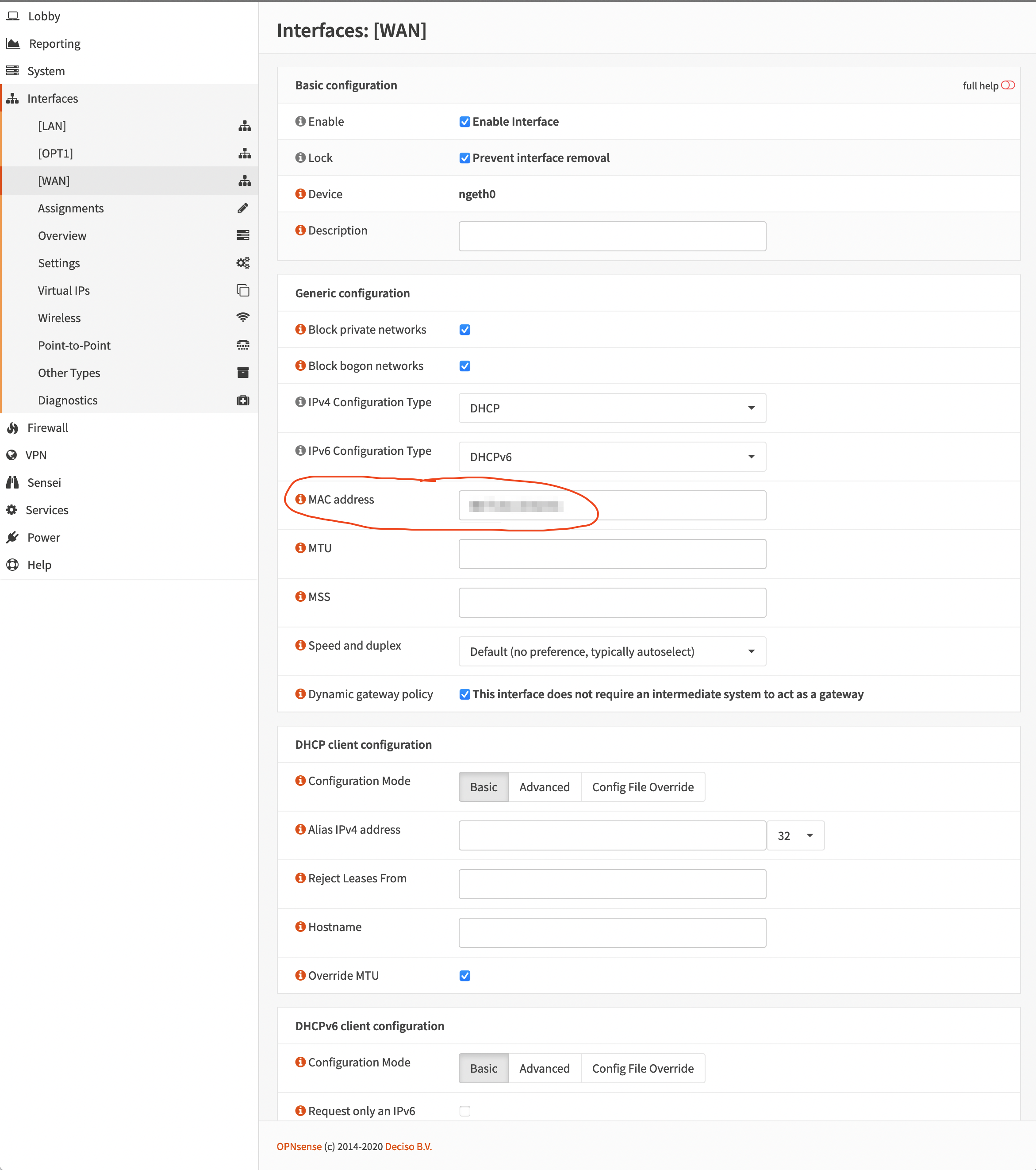
OPNsense network interface configurations are somewhat straight forward. All three interfaces LAN, OPT1 and WAN are pictured below with pi-hole running as the DNS server at 192.168.1.102.
[LAN]
[OPT1]
[WAN]
Don’t forget to spoof the MAC address RG_ETHER_ADDR here.
cal
Firewall
We’re almost done. Home Network Guy does a fantastic job of describing how to setup the OPNsense firewall rules here
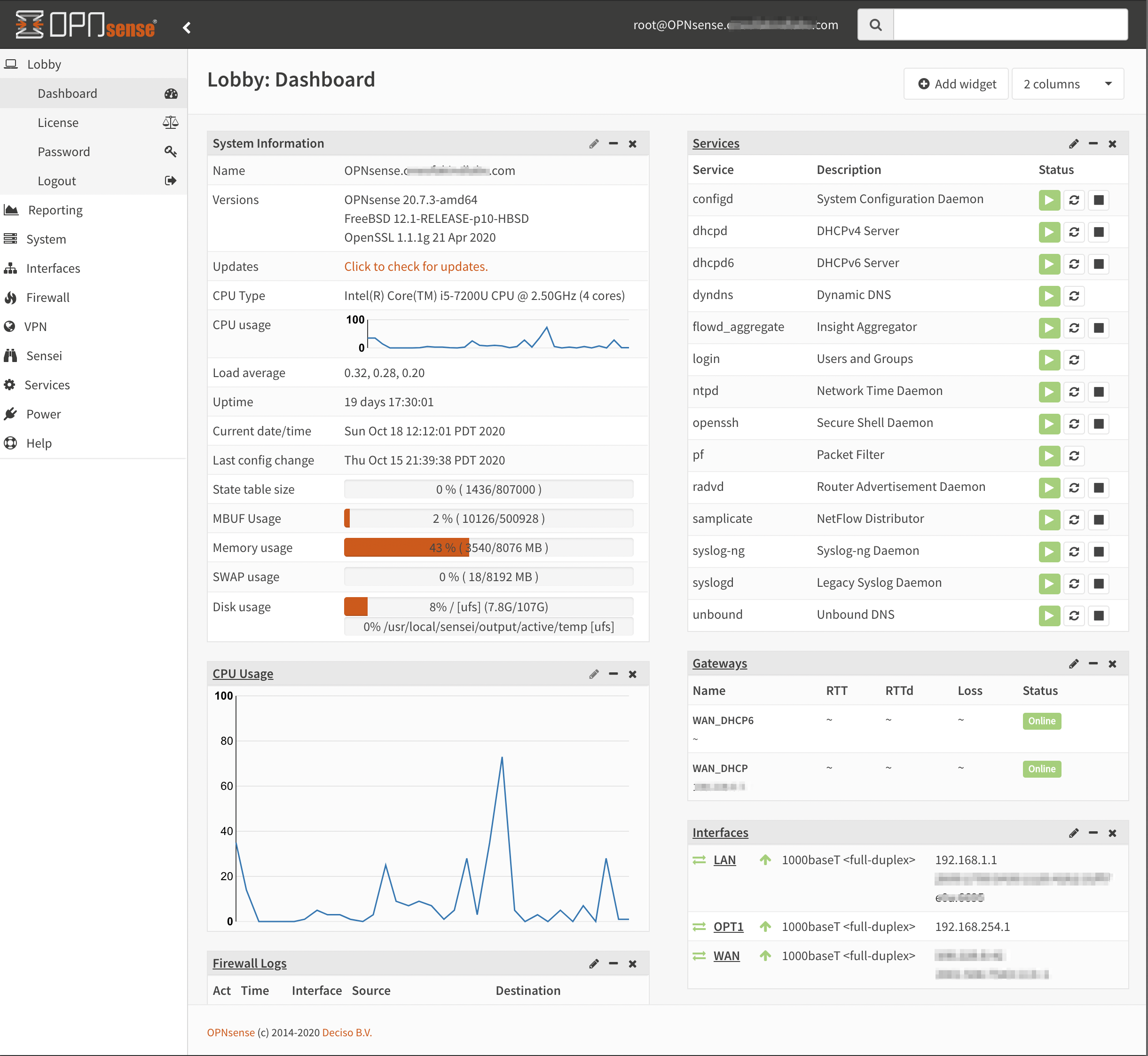
Lobby Dashboard
Once everything is setup, the lobby dashboard looks like this: